openbsd
"Happy Birthday, Linuks"
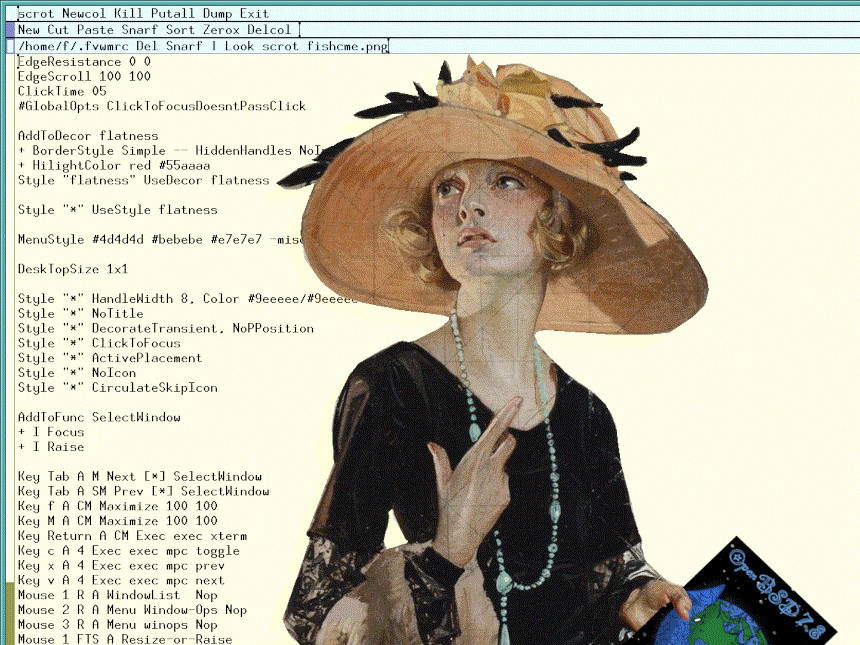
rio-like configuration for base openbsd fvwm2
#UseBSD #RUNBSD #BSD #FOSS #UNIX
#UseBSD #RUNBSD #BSD #FOSS #UNIX #Linux
Advertisement: We are happy to welcome our new sponsor at #BoxyBSD: ST-Hosting.com
ST-Hosting.com stands for performance, stability, and pragmatic solutions and hosting like:
- LXC & KVM servers on AMD EPYC, Ryzen, Intel Xeon systems
- Fair pricing and direct support from Germany
- Hosting made in Germany
We’re excited to have https://st-hosting.com on board! You can immediately start to provision your BSD based boxes (like #FreeBSD, #OpenBSD, #NetBSD,...) at BoxyBSD in our new location in Germany, Nuremberg. Also, stay tuned for #Fosdem ;) Thanks a lot!
Static Web Hosting on the Intel N150: FreeBSD, SmartOS, NetBSD, OpenBSD and Linux Compared
Update: This post has been updated to include Docker benchmarks and a comparison of container overhead versus FreeBSD Jails and illumos Zones.
#ITNotes #freebsd #illumos #jail #linux #netbsd #openbsd #ownyourdata #server #smartos #sysadmin #zoneshosting
XTerm*faceSize: 10
is this just the same does it not matter ?
xterm*faceSize: 10
Sorry but if it does not matter, if I start XTerm or xterm then that's good as having both just now plays on my OCD. :D
Does anyone manage to use the #keyboard media controls in #FreeBSD #Xorg? I have a DasKeyboard with a volume jog that works out of the box on #OpenBSD.
The events seems to be working using xev tester. It regognizes the RaiseVolume and LowerVolume events.
Not sure where to actually start looking for a solution.
The slides, the video, and the text behind my presentation at EuroBSDCon 2024 - 'Why and how we're migrating many of our servers from Linux to the BSDs.'
https://it-notes.dragas.net/2024/10/03/i-solve-problems-eurobsdcon/
#ITNotes #FreeBSD #OpenBSD #NetBSD #RunBSD #IT #SysAdmin #EuroBSDCon #EBC24 #EuroBSDCon24 #EuroBSDCon2024 #NoteHUB
https://github.com/macports/macports-ports/pull/27712
GitHub Continuous Integration checks are running. Hopefully they will be OK (Update 2 out of 3 have completed successfully, which is a good sign).
I tested locally without issues, but I also build against LibreSSL locally, whereas GitHub CI and MacPorts' Build Bots I think default to OpenSSL.
This release is to address some vulnerabilities identified by Qualys and other less critical bugs.
More details from upstream here:
https://www.openssh.com/releasenotes.html#9.9p2
Of particular note:
" Fix CVE-2025-26465 - ssh(1) in OpenSSH versions 6.8p1 to 9.9p1
(inclusive) contained a logic error that allowed an on-path
attacker (a.k.a MITM) to impersonate any server when the
VerifyHostKeyDNS option is enabled. This option is off by default.
* Fix CVE-2025-26466 - sshd(8) in OpenSSH versions 9.5p1 to 9.9p1
(inclusive) is vulnerable to a memory/CPU denial-of-service related
to the handling of SSH2MSGPING packets. This condition may be
mitigated using the existing PerSourcePenalties feature.
Both vulnerabilities were discovered and demonstrated to be exploitable
by the Qualys Security Advisory team. We thank them for their detailed
review of OpenSSH."
If I read everything correctly, these vulnerabilities primarily only impact the Portable OpenSSH releases (which is what MacPorts uses). However, OpenBSD has also issued the following errata to mitigate one of the issues as it also appears to impact OpenBSD users:
"008: SECURITY FIX: February 18, 2025 All architectures
sshd(8) denial of service relating to SSH2MSGPING handling. ssh(1) server impersonation when VerifyHostKeyDNS enabled.
A source code patch exists which remedies this problem."
Source code patch for OpenBSD here:
https://ftp.openbsd.org/pub/OpenBSD/patches/7.6/common/008_ssh.patch.sig
Having written as much, it appears as if the main OpenSSH version for OpenBSD is still 9.9, so I am not going to make a submission for undeadly.org Other editors reading this are welcome to though, I just kind of have a lot of other stuff on my plate at present.
As usual, I also have too much going on in my life to want more responsibilities such as commit access within MacPorts, so it's up to someone else to merge it.
Update #2: I also decided to be a good Samaritan and reported the issue to Apple. Not that they have ever acknowledged my efforts for such things nor paid me from their bug bounty program in years of doing similar things. Because, OFC, Apple can't spare a penny to anyone like me. Maybe Qualys already reported it to them anyway (though they would have no obligation to do so, they did find the vulns and reported them upstream as would be expected).
#OpenSSH #MacPorts #SecureShell #InfoSec #Cryptography #Security #CVE #PatchTuesday #OpenSource #OpenBSD #macOS
Is everything terrible again? Let's focus on something completely different. Do you write amazing, perfect code on Linux or the BSDs? Well stop reading and get out. For the rest of us, how do we secure our systems? I've put together a survey on Source Code Sandboxing, https://kristaps.bsd.lv/devsecflops, which surveys the practical complexity and uptake of sandbox tools like seccomp, landlock, pledge, and capsicum.
If you've ever interfaced any of the tools I've mentioned, or want to mention another, head on over to https://github.com/kristapsdz/dev_sec_flops and make a pull request.
Enjoy! #Linux #openbsd #freebsd #programming
FYI, S3 suspend/wakeup works flawlessly with #FreeBSD and #OpenBSD on this laptop without any hack.
#BSD #RunBSD #Unix #FOSS
List of hosts for #remotePuterRental collected from others' queries, with URLs on first reference where provided …
https://mastodon.bsd.cafe/@emilianosandri/115543215260941334
20251113, re #BSD-friendly European cloud provider (using Contabo with no issues):
— #FreeBSD: Hetzner https://www.hetzner.com/cloud/ -may need to supply own custom image, etc; Netcup; OVH;
— {Free,Open}BSD: TransIP;
— #OpenBSD: OpenBSD Amsterdam https://openbsd.amsterdam/ .
…
I've been gifted a Thinkpad X220 that's been lying dormant a number of years.
Instead of my usual Debian I _was_ going to install Arch, but now I'm thinking of making it a dedicated BSD machine. Going to give OpenBSD a go. 
Bob Beck (OpenBSD) on why vi should be and stay vi.
#OpenBSD #vi
https://marc.info/?l=openbsd-misc&m=115820462402673&w=2
I have a theory about 6-month Linux and BSD upgrades having their own kind of "stability" because there's not as far to go between releases https://zola.passthejoe.net/blog/six-month-stability/
The configuration is very simple and once in place is set and forget.
Do not roll out IPv4 for any new deployments. Also think about migrating away from dual stack.
#OpenBSD